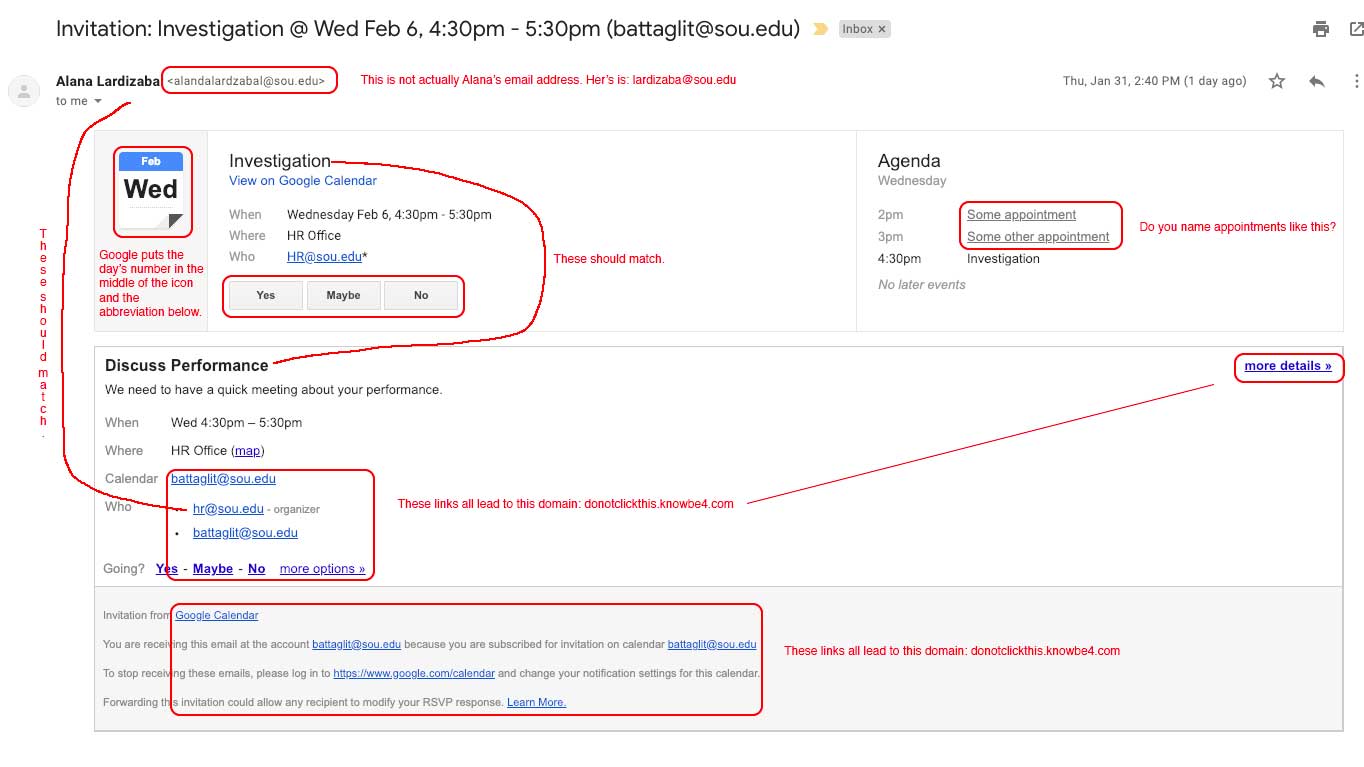
This email appointment is a sample of a "Spear-Phishing" attack. Spear-Phishing is when attackers use specific information that relates closely to you and/or your organization. Spear-phishing is one of the most successful techniques that attackers use to compromise systems and people.
1. The first thing to notice is that the email address for Alana is actually incorrect. This is difficult to spot, but it is something an attacker may get wrong.
2. The email subject line, and the appointment title both read, "Investigation," yet the subtitle reads, "Discuss Performance." In an authentic appointment, these would all read the same.
3. In the "Agenda" section, notice that the other calendar details read simply, "Some appointment" and "Some other appointment." An attacker would likely not be able to know the details of your calendar, thus they would have to fill this in with something generic or inaccurate.
4. In an authentic appointment, the "organizer" should be the same as the sender. This won't always be true. For example, a delegate can send an appointment for someone else's calendar. However, an attacker would need to know the names of both people. Generally, it will be the same identity in both places.
5. As with the other emails in this simulation, all of these links lead to the suspicious domain: dontclickthis.knowbe4.com .
6. Last, it's difficult to spot, but the icon on the left side of the appointment should have the number "6" in its middle with the abbreviation, "Wed" beneath it.